Hi QC,
I'd like to continue this discussion, first thing first, our Sophos gateway is the old firewall from Cisco and we want to migrated it to the new firewall from Palo Alto.
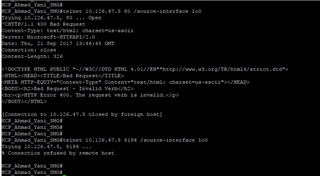
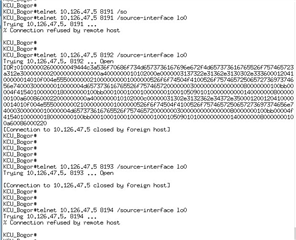
When we tried to migrated it to the new Firewall, all of thousands of clients could connect to port 80 or 8192 just fine, but cannot connect to port 8194.
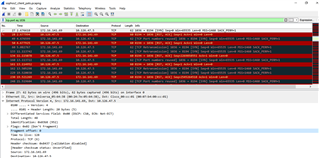
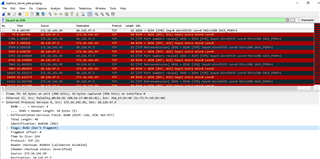
As we dig deeper, the RMS server couldn't telnet localhost 8194 even though it was a local connection to the server itself.
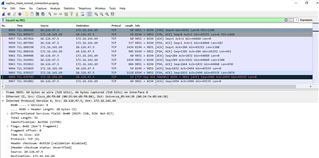
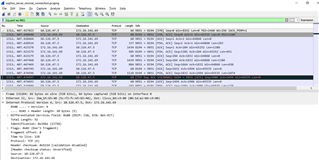
From wireshark pcap, we saw that the RMS sent TCP RST ACK for all the TCP SYN attempts from all the clients.
We tried to open the case to Palo Alto support and they said there was no drop at the Firewall at all, we even remove any inspection for the traffic to Sophos server at the Firewall.
But if we revert back the migration back to the old Firewall, port 8194 will comes back online again and everything going back to normal.
I attached some of the logs from the Sophos at the normal condition and migration (failed) condition.
Please tell me if you need another log.
Thank you.
This thread was automatically locked due to age.