Hi Experts :) ,
I am facing an issue with the following ESC. We have Windows 7 and 10 OS installed in our environment. Below is the error I am getting.
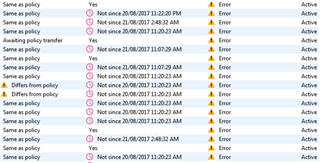
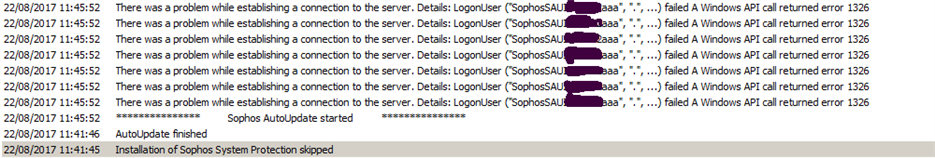
Actually the Update is failing with the below error, and sometimes it updates successfully but next moment if I check it says Failed and the reason shows account locked. Whereas I've also checked the account in local machines its not locked.
Would highly appreciative if I get quick response and support in solving this issue.
Please find error attached.
Thanks
Best Regards
Faisal
This thread was automatically locked due to age.