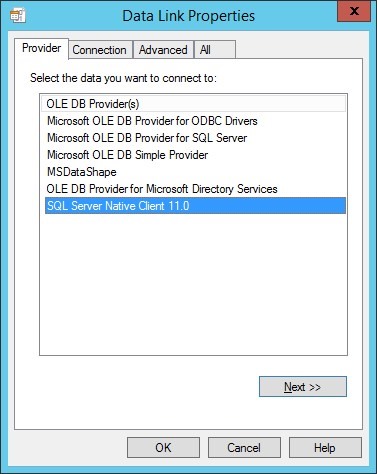
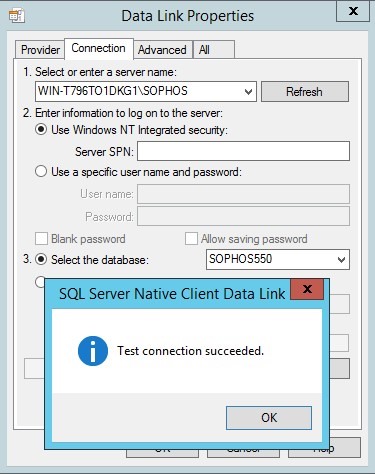
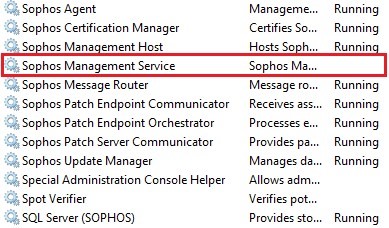
In order to be PCI compliant we have a requirement to disable TLS 1.0 on the Windows 2012 R2 server running the Enterprise Console version 5.5.0
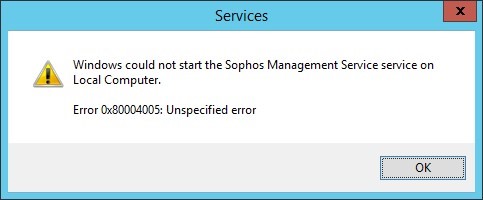
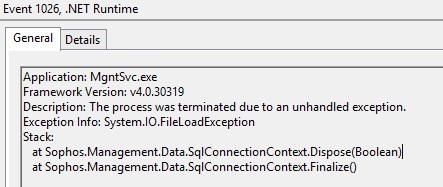
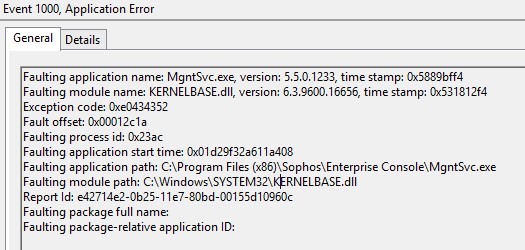
When i disable TLS 1.0 the Sophos Management Service fails to start with
event ID 8025 There is no database connection. Management Service will be shut down.
and event ID 8004 Initialization failed.
Step: Creating a database connection
Error: std::runtime_error
Data: [DBNETLIB][ConnectionOpen (SECDoClientHandshake()).]SSL Security error.
I initially raised a call with Sophos and it was closed saying the issue was fixed in version 5.4.1 of the console which i was running at the time,
i have now upgraded to version 5.5.0 and the issue still exists
This thread was automatically locked due to age.