Hi,
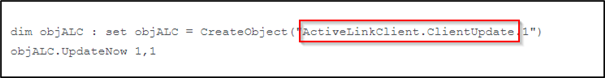
As some might have found out, there are some command/actions that can be done through COM objects. Example, trigger an update in the endpoint through command line:
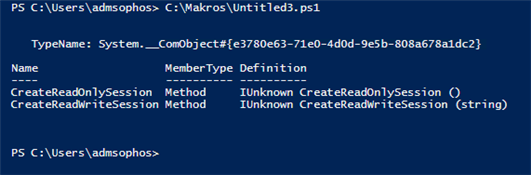
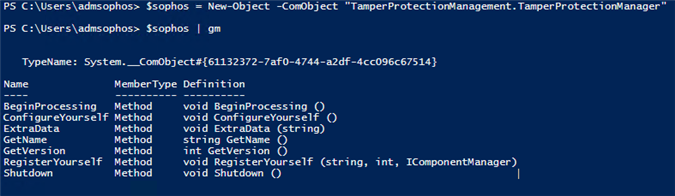
So, after checking the COM objects of Sophos, end up finding all of these (perhaps some non-Sophos got in, but are the less)
[locked by: Sure Win at 12:42 PM (GMT -7) on 25 May 2018]
[unlocked by: Sure Win at 12:42 PM (GMT -7) on 25 May 2018]
[locked by: Sure Win at 12:43 PM (GMT -7) on 25 May 2018]