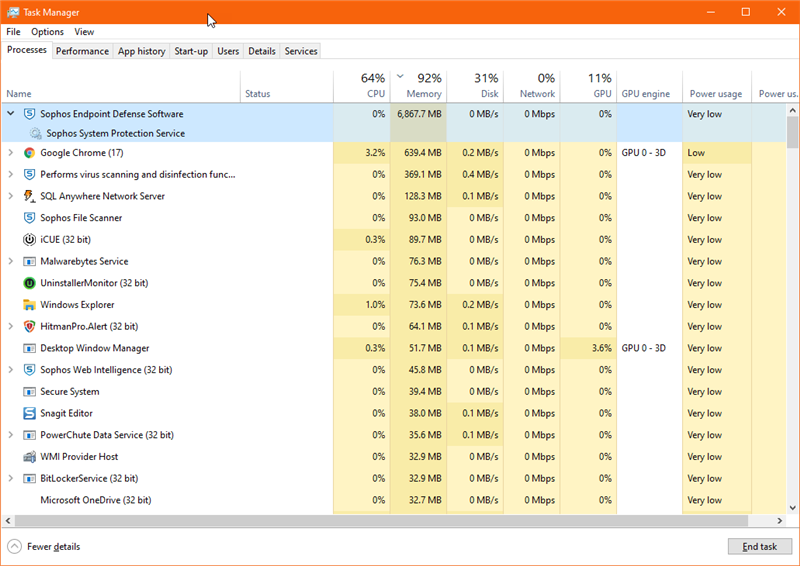
Currently have Sophos Central with Sophos Endpoint running on several machines here, i was the first to update to the latest Windows 10 1903 Update and noticed after the machine sitting idle for a while that the above service is consuming a lot of RAM.
Any solutions to this?
This thread was automatically locked due to age.