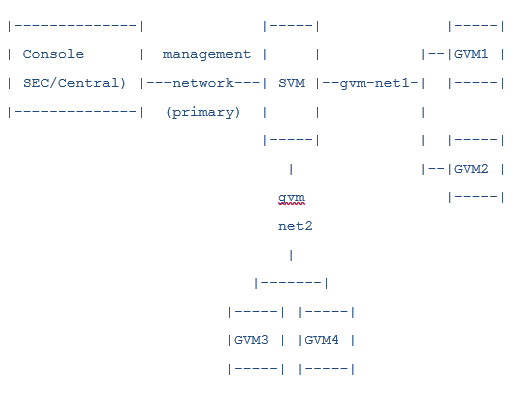
Now shipping with all Server Protection licenses, Sophos for Virtual Environments is designed to efficiently secure virtual servers and desktops running on either VMware vSphere or Microsoft Hyper-V. By offloading malware detection to a centralized Security Virtual Machine, Sophos for Virtual Environments conserves critical resources on each guest machine, and eliminates scan and update storms.
- Provides real-time threat protection and automated clean-up
- Easy and flexible deployment; supports multiple hypervisors
- Manage using Sophos Enterprise Console or Sophos Central
- Included with all Sophos Server Protection licenses
Learn more:
Note: Sophos for Virtual Environments replaces the Sophos AntiVirus for vShield product; existing vShield customers now have automatic entitlement to Sophos for Virtual Environments within their existing license.
Thanks
Mark
This thread was automatically locked due to age.