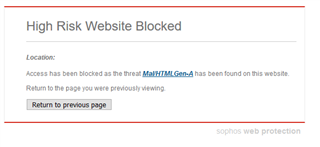
Anyone know why Sophos endpoint software kicks up this message when trying to access an ESXI host by its IP address?
Sophos endpoint advanced 10.8.3 with core agent 2.2.2 is what is installed on my windows box.
I can rebuild any ESXI6.7 u1 or u2 from the official VMware ESXI iso's , tried both modified & standard versions and I get this Sophos message every time when trying to connect to the ESXI host by its IP address.
If I use the FQDN of the host , I do not get the message - this happens on all browsers where Sophos endpoint is installed.
Any info would be greatly appreciated.
This thread was automatically locked due to age.