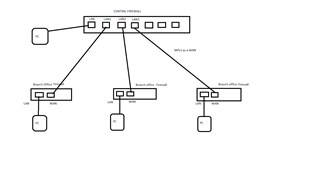
Hi Guys,
I had a question about Sophos Heartbeat issue. I am attaching the network diagram. In short, there is a central firewall (XG) and all the branch firewalls (XG) are connected via MPLS as a WAN ( they get their internet from the central firewall ) . All branches and the central firewall all have endpoints which are installed with the CIXA ( only one central account for all the firewalls and branches ). We have synchronized each of the branch firewalls with the single central account. My question is, is it possible to see ALL the branch endpoints to send their heartbeat status to the central firewall ONLY. We dont mind de-registering the branch office firewalls for synchronized security. Is this possible ?
This thread was automatically locked due to age.